Dowser
Learning to bodge again..
Blocking incoming connections won’t do anything to help or secure things.
Creating VLANs won’t do anything to help or secure things.
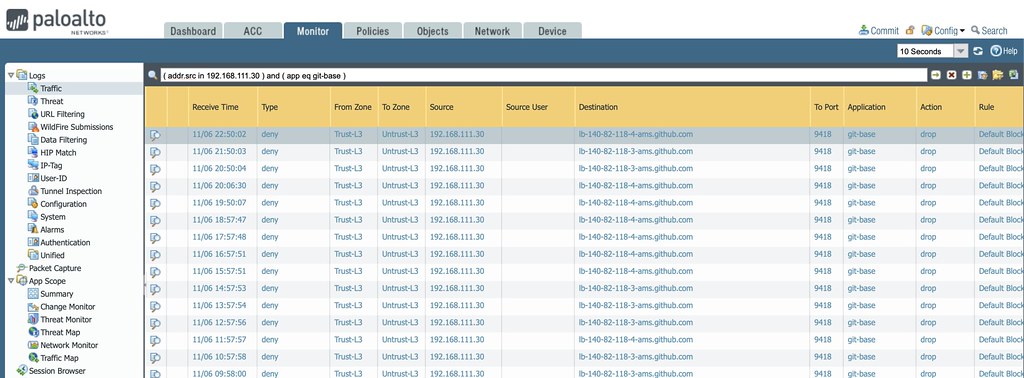
Huh? My QNAP is not visible to the internet, I am running no services on it that requires it to do so. I am not blocking anything to the QNAP per se, I just have a zero trust policy and ensure whatever internet access router I have only allows in>out initiated connections. Zero incoming Udp/tcp allowed, default drop rule first in my list
I think you need to qualify your statement?